

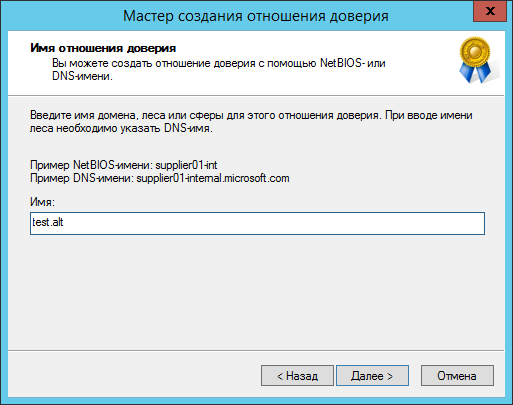

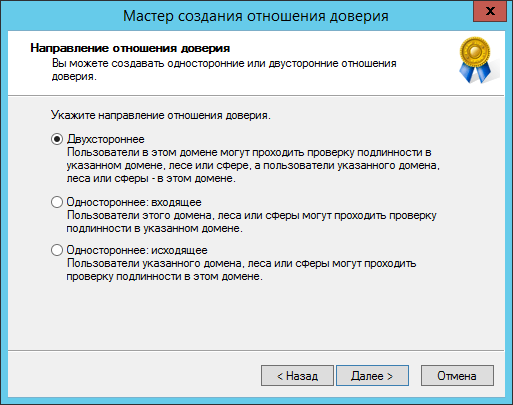
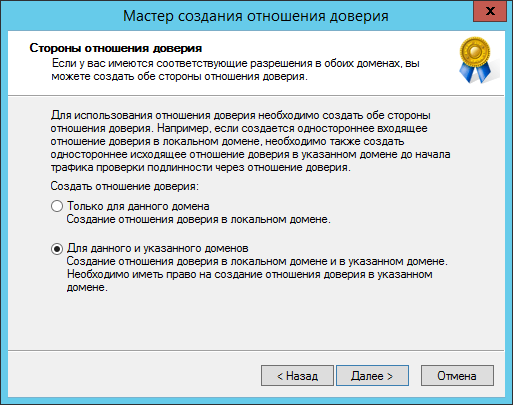
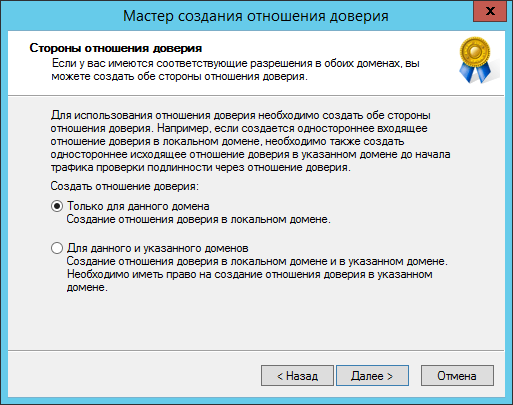
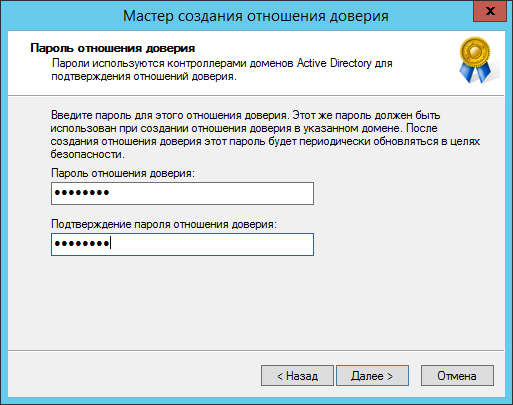
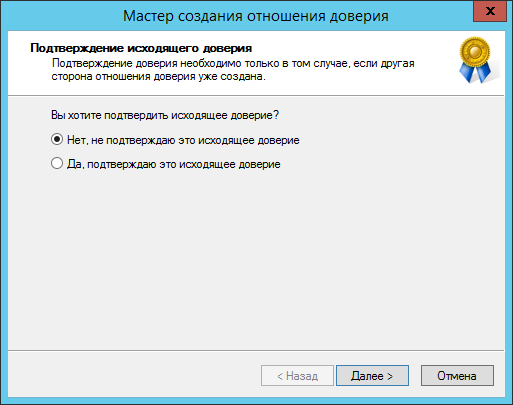
Примечание
# samba-tool domain trust create win.alt --type=forest \
--direction=both --create-location=both -Uadministrator@WIN
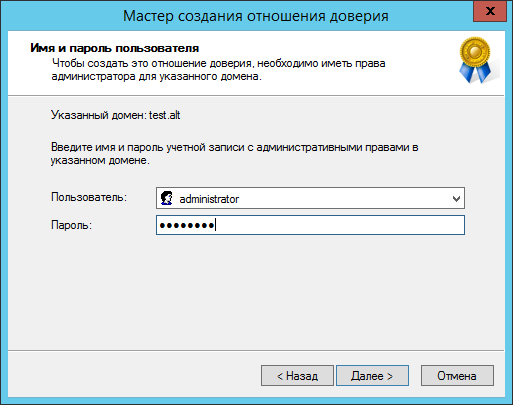
При появлении запроса необходимо ввести пароль администратора.
Важно
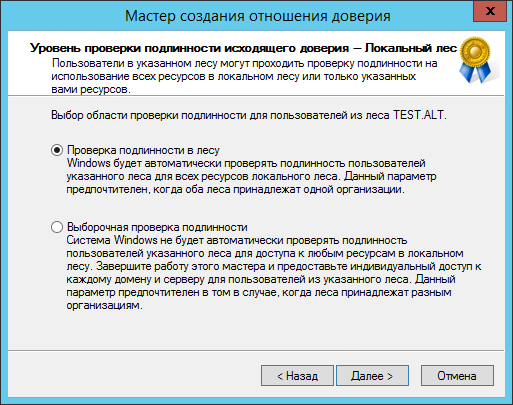
external, а не forest.
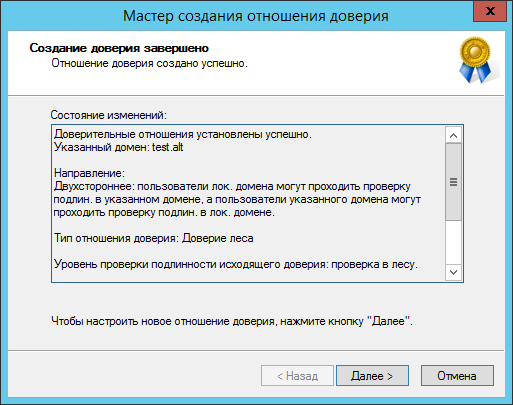
LocalDomain Netbios[TEST] DNS[test.alt] SID[S-1-5-21-3848605173-1839566900-710408900] RemoteDC Netbios[DC1] DNS[DC1.win.alt] ServerType[PDC,GC,LDAP,DS,KDC,TIMESERV,CLOSEST,WRITABLE,GOOD_TIMESERV,FULL_SECRET_DOMAIN_6,ADS_WEB_SERVICE,DS_8,__unknown_00008000__] Password for [administrator@WIN]: RemoteDomain Netbios[WIN] DNS[win.alt] SID[S-1-5-21-212759798-1661061060-862600140] Creating local TDO. Local TDO created Setting supported encryption types on local TDO. Setup local forest trust information... Namespaces[2] TDO[win.alt]: TLN: Status[Enabled] DNS[*.win.alt] DOM: Status[Enabled] DNS[win.alt] Netbios[WIN] SID[S-1-5-21-212759798-1661061060-862600140] Validating outgoing trust... OK: LocalValidation: DC[\\DC1.win.alt] CONNECTION[WERR_OK] TRUST[WERR_OK] VERIFY_STATUS_RETURNED Validating incoming trust… OK: RemoteValidation: DC[\\dc1.test.alt] CONNECTION[WERR_OK] TRUST[WEER_OK] VERIFY_STATUS_RETURNED Success.
--create-location нужно заменить опцию both на local. Samba DC прежде чем создать доверительные отношения сначала запросит Trust Key (Incoming Trust Password/Outgoing Trust Password), созданный ранее при настройке в Windows:
# samba-tool domain trust create win.alt --type=forest \
--direction=both --create-location=local -Uadministrator@WIN
New Incoming Trust Password:
Retype Incoming Trust Password:
New Outgoing Trust Password:
Retype Outgoing Trust Password:
LocalDomain Netbios[TEST] DNS[test.alt] SID[S-1-5-21-3848605173-1839566900-710408900]
RemoteDC Netbios[DC1] DNS[DC1.win.alt] ServerType[PDC,GC,LDAP,DS,KDC,TIMESERV,…]
Password for [administrator@WIN]:
…
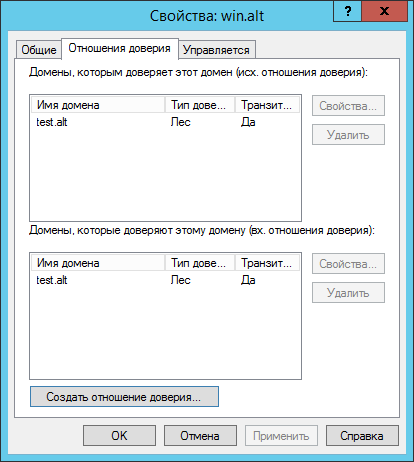
# samba-tool domain trust show WIN.ALT
LocalDomain Netbios[TEST] DNS[test.alt] SID[S-1-5-21-3848605173-1839566900-710408900]
TrustedDomain:
NetbiosName: WIN
DnsName: win.alt
SID: S-1-5-21-212759798-1661061060-862600140
Type: 0x2 (UPLEVEL)
Direction: 0x3 (BOTH)
Attributes: 0x8 (FOREST_TRANSITIVE)
PosixOffset: 0x00000000 (0)
kerb_EncTypes: 0x18 (AES128_CTS_HMAC_SHA1_96,AES256_CTS_HMAC_SHA1_96)
Namespaces[2] TDO[win.alt]:
TLN: Status[Enabled] DNS[*.win.alt]
DOM: Status[Enabled] DNS[win.alt] Netbios[WIN] SID[S-1-5-21-212759798-1661061060-862600140]
# samba-tool domain trust list
Type[Forest] Transitive[Yes] Direction[BOTH] Name[win.alt]
# samba-tool domain trust validate win.alt -Uadministrator@WIN
LocalDomain Netbios[TEST] DNS[test.alt] SID[S-1-5-21-3848605173-1839566900-710408900]
LocalTDO Netbios[WIN] DNS[win.alt] SID[S-1-5-21-212759798-1661061060-862600140]
OK: LocalValidation: DC[\\DC1.win.alt] CONNECTION[WERR_OK] TRUST[WERR_OK] VERIFY_STATUS_RETURNED
OK: LocalRediscover: DC[\\DC1.win.alt] CONNECTION[WERR_OK]
RemoteDC Netbios[DC1] DNS[DC1.win.alt] ServerType[PDC,GC,LDAP,DS,KDC,TIMESERV,CLOSEST,WRITABLE,GOOD_TIMESERV,FULL_SECRET_DOMAIN_6,ADS_WEB_SERVICE,DS_8,__unknown_00008000__]
Password for [administrator@WIN]:
OK: RemoteValidation: DC[\\dc2.test.alt] CONNECTION[WERR_OK] TRUST[WERR_OK] VERIFY_STATUS_RETURNED
OK: RemoteRediscover: DC[\\dc2.test.alt] CONNECTION[WERR_OK]